Balancing Border Security: Conventional Methods and Contemporary Means
By Major Nick Bennett and Doctor Richard Warnes PhD
Border Security in the context of counter-terrorism (CT) has long been a topic of debate in terms of how a government can balance its resources to provide protection to its population. Over the past decade, terrorism has, on average, accounted for around 24,000 deaths per year, with cross-border terrorist attacks remaining a continuous threat and vulnerability for most countries. This does not factor in the impact of cross-border planning for terrorist attacks, and also the crime-terrorism nexus, whereby cross-border criminal activity directly funds terrorist activity. The overarching picture is that border security is a vital component in a government’s wider CT measures. As such, from a policy level down to tactical implementation, understanding the threats and how to balance conventional methods with contemporary means is essential to providing coherent and long-lasting security.
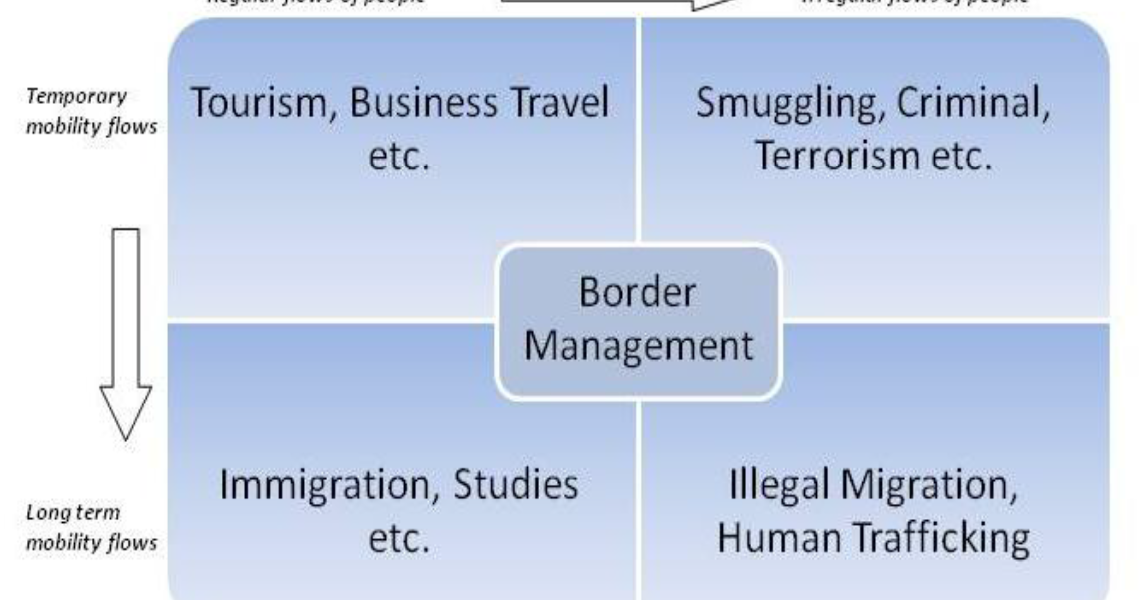
However, governments must also balance the need for secure borders with the economic requirement to maintain a flow of people and goods across the border in order to maintain trade and/or tourism. While the scale of this balance will clearly depend on the threat and level of operational permissiveness around the border, there is usually a trade-off that has to be made between ensuring security while maintaining the level of flows. When considering these flows of people and goods in relation to border management, there is also a distinction to be made between temporary and longer-term flows, as well as between regular and irregular flows. This concept regarding types of flow and their link to the management of the border, has previously been outlined in a report on the ‘Futures of Borders’ by the European Border Agency FRONTEX.
There are various factors that should be considered when establishing, improving or maintaining border security. Various case studies can help draw attention to this; three excellent examples are: Lebanon, Türkiye and Tunisia. All of which emphasise the need for a balanced approach to border security, outlining the challenges of the 21st Century and why a government cannot discard conventional methods, nor shy away from investment in technology. These lessons are particularly relevant in areas where borders are either contested or militarised.
Control or Security?
While it can be acknowledged border security is a reasonably abstract term with no clear consensus in definition, the aim of border security can be understood primarily in terms of what it is not. Namely, border control and border protection. Figure 1 demonstrates where border security is relevant by comparison to other mechanisms used. Whereas control exists on most borders to manage goods and people, and protection also exists to mitigate against varying degrees of violence or criminality, security can be understood, in the context of counter-terrorism, to be a term that guards a nation’s borders against acts of terrorism. There is obviously a wider use to this term, that encompasses state and non-state threats, though in the context of this article, the term relates to terrorism.
Placing the requirement for border security in a geographical sense is equally a difficult task. Arguably most countries in the world would opt for a form of ‘border security’ against terrorism, though arguably the term can be too easily conflated with the aforementioned terms – border control and protection. The problem with doing so, is that every issue regarding a border can be viewed as a ‘security’ matter, and thus a government risks consciously or inadvertently engaging in the process of securitisation – whereby political matters are conveyed as extreme security problems, resulting in political bandwidth and resources being focused on areas that do not require it.
Border security as a concept should be applied to those borders where the situation reaches a point of operational and tactical complexity, and security measures can be used to allow policy-makers time and space to develop longer lasting plans. Or, where the threat level is such that control and protection mechanisms are no longer sufficient to manage the possible consequences of terrorists accessing the border. In these circumstances, a balance of conventional methods as well as contemporary developments are required to effectively mitigate potential or actual acts of terrorism.
Conventional methods – an insight into the Lebanese border
Using Lebanon as a case study, a practitioner or academic, can gain a valuable insight into how conventional methods still hold a great deal of value, not least where the ground beyond a country’s sovereignty territory is ungoverned or permissible to terrorist groups. At the height of the Syrian Civil War, where Da’esh had gained territorial control of large swathes of the country, the terrorist group attempted to make various ground incursions into Lebanon. Being a small state, Lebanon does not benefit from the strategic depth of terrain. At its widest point, the distance is only around 35 miles from the Syrian border to Beirut on the coast. Therefore, security at the borders is paramount to protecting the state – both physically and politically.
With assistance primarily from the UK and US, Lebanese Armed Forces (LAF) were able to harden their borders, constructing physical outposts along the border with Syria. This served a number of purposes, but crucially, it defined the border area and then allowed for an operational platform to exist. Having secure areas to defend, then permitted the LAF to expand their operations, patrolling the areas in-between and providing integral and organic mutual support between positions.
The drawback of this approach is that it is underpinned by shorter-term investments, the approach is far more linear in terms of understanding and responding to threats, and as the measures tend to be more static, the security stance is less proactive. Ultimately, in the areas where border security is required, policies need to be developed where more contemporary means are employed to complement conventional methods.
Contemporary means – embracing technology on the Turkish borders
The measures that a state can take to enhance border security using technological means are not exhaustive. Primarily, the use of data – collecting, processing and exploiting – is one of the fundamental means of developing border security. This point is wider than simply collecting biometrics and processing goods and individuals at borders, an activity that would fall into the category of ‘control’ or ‘protection’. While this data is useful in border security, there is more that can be harnessed from the collection of data.
Concepts such as machine learning and artificial intelligence, as well as the use of sensors, are predominantly driven by data collection, and it is this that can be used in contested and high-threat areas to complement conventional methods. The use of higher-end technology to aid human decision-making is arguably how the most secure borders will operate in the future, if not already. Figure 3 is illustrative of how technological assets can be integrated with ‘hardened’ security features to allow for more informed and data driven human decision-making. So-called ‘Smart-Borders’ utilise sensors that will collect data and drive machine learning and AI-based assets to dynamically assess threats and over time improve their ability to provide more comprehensive border security.
Using Türkiye as a case study, it is possible to see how this type of technology can be used to counter terrorist activity on borders. Türkiye is a great example of a country that has to contend with myriad terrorist threats, enhanced by the geographical terrain that surrounds them, and compounded by the flow of refugees that seek entry into the country. Most notably, the PKK operate in ungoverned space beyond Türkiye’s borders, as do Da’esh and AQ. Türkiye has opted to invest heavily in technology as a means to future-proof their border security, using an integrated system of masts that have surveillance radars, gunshot detection systems and wireless sensors. The result is to complement existing structures, and intelligently focus on areas where threats are higher, using technology to provide cover in border areas where the threat of terrorist activity can be less easily detected by human resources.
Conventional methods and Contemporary means – a hybrid approach on the Tunisian borders
The example of Tunisia provides a useful example of a hybrid approach to the security of its borders, combining both physical barriers and patrols to ‘harden’ the border, along with the introduction of advanced technology to detect threats, alert border personnel and collect data and intelligence. Tunisia’s borders predominantly combine underpopulated desert and mountainous areas, with terrorist threats emanating from both its Algerian and Libyan borders. This is particularly the case with the ‘ungoverned space’ of Libya, with two high-profile terrorist attacks in Tunisia against tourists in 2015 linked to Da’esh networks in Libya. The following year, a cross border raid by up to 100 Da’esh fighters led to two days of heavy fighting between Tunisian security forces and Da’esh fighters in the border city of Ben Guerdane.
In response to these incidents, Tunisia constructed sand berms and major water filled trenches along the Libyan border. More recently fencing has been added, and these physical barriers are regularly patrolled by Tunisian armed forces and border security personnel. With the support of various countries, Tunisia has enhanced these conventional physical measures with technical sensors, intruder detection and surveillance technology, particularly in the more remote desert areas between the two countries.
However, the integration of technological systems is costly. Arguably, the cost is higher initially, though technology will still evolve, and so there is likely to be a continued financial burden to properly use this type of border security. Governments need to address this in a number of ways. The first, is to invest heavily in national defence industry, providing the economic incentives to allow the private sector to grow. The second, is to forge closer links between the areas of the military and law enforcement organisations that specialise in border security, and private companies. This should allow for intelligence sharing, research and development in conjunction with operational border security organisations, and a programme of military placements into commercial organisations. Finally, there should be greater collaboration on an inter-state basis, to share technology and benefit from the unique insights and experiences that each country has regarding their own border security circumstances.
Conclusion
The nature of border security with regards to counter-terrorism is complex and constantly evolving. The first, and crucial, component is to understand what is actually meant by border security in relation to CT, and applying this academically before then taking practical measures. Ultimately, borders are too often prone to ‘securitisation’, and so are conflated with measures that would more appropriately be categorised as control or protection.
Furthermore, governments should not forget conventional methods of border security. Hardening of borders in light of credible terrorist activity and the use of ground patrolling is likely to not only provide a human dimension to any wider security matrix, but will also act as a very visible deterrent in its own right. In cases such as Lebanon, where strategic depth cannot be achieved geographically, conventional border security measures are not just useful, but essential.
However, as with Lebanon, Türkiye and Tunisia there are examples of how technology and contemporary means have driven new border security measures, in the face of evolving terrorist threats. The ability to harness data, particularly in more contested environments where threat levels are higher, will ultimately feed the hardware needed to provide more comprehensive layers of security. Additionally, having a solid defence industry as a base, coupled with a culture that promotes interaction between military, law enforcement and the private sector is key to staying ahead of technological shifts.
In terms of countering terrorism, smart borders are likely to be crucial in the fight to maintain sovereignty of borders and protect those that live within them. However, governments need to balance conventional methods with contemporary means in order to maximise their ability to both proactively deter threats, but also react to terrorist attacks.